SharkBot Banking Malware Spreading through Faux Android Antivirus App on Google Play Retailer
The risk actor behind a nascent Android banking trojan named SharkBot has managed to evade Google Play Retailer safety boundaries by masquerading as an antivirus app.
SharkBot, like its malware counterparts TeaBot, FluBot, and Oscorp (UBEL), belongs to a class of economic trojans able to siphoning credentials to provoke cash transfers from compromised units by circumventing multi-factor authentication mechanisms. It first emerged on the scene in November 2021.
The place SharkBot stands aside is in its potential to hold out the unauthorized transactions through Automated Switch Techniques (ATS), which stands in distinction to TeaBot, which requires a reside operator to work together with the contaminated units to conduct the malicious actions.
“The ATS options permit the malware to obtain an inventory of occasions to be simulated, and they are going to be simulated as a way to do the cash transfers,” Alberto Segura and Rolf Govers, malware analysts at cybersecurity agency NCC Group, mentioned in a report revealed final week.
“Since these options can be utilized to simulate touches/clicks and button presses, it may be used to not solely robotically switch cash but additionally set up different malicious functions or parts.”
In different phrases, ATS is employed to deceive the focused financial institution’s fraud detection techniques by simulating the identical sequence of actions that will be carried out by the consumer, corresponding to button presses, clicks, and gestures, as a way to make the illicit cash switch.
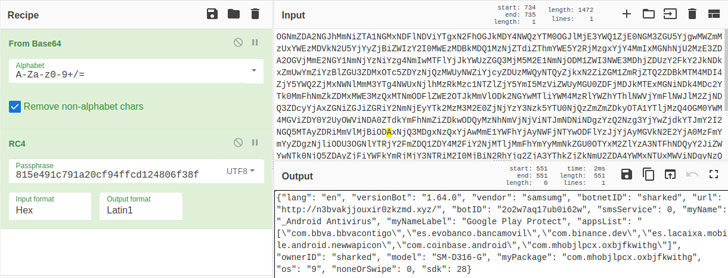
The newest model noticed on the Google Play Retailer on February 28 are a lot of dropper apps that additionally leverages Android’s Direct Reply performance to propagate itself to different units, making it the second banking trojan after FluBot to intercept notifications for wormable assaults.
The checklist of malicious apps, all of which have been up to date on February 10, have been collectively put in about 57,000 instances thus far –
SharkBot can be feature-rich in that it allows the adversary to inject fraudulent overlays atop official banking apps to steal credentials, log keystrokes, and procure full distant management over the units, however solely after the victims grant it Accessibility Companies permissions.
The findings come per week after researchers from Cleafy disclosed particulars of a brand new TeaBot variant discovered within the Play Retailer that is designed to focus on customers of greater than 400 banking and monetary apps, together with these from Russia, China, and the U.S.