Over 300,000 MikroTik Units Discovered Susceptible to Distant Hacking Bugs
A minimum of 300,000 IP addresses related to MikroTik units have been discovered susceptible to a number of remotely exploitable safety vulnerabilities which have since been patched by the favored provider of routers and wi-fi ISP units.
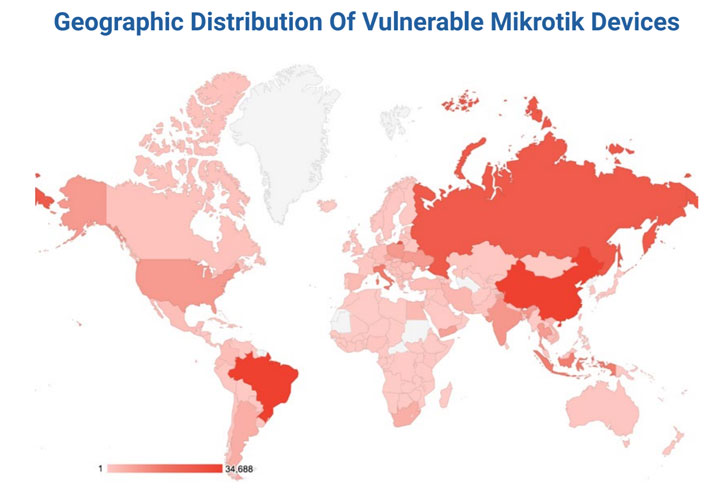
Essentially the most affected units are situated in China, Brazil, Russia, Italy, Indonesia, with the U.S. coming in at quantity eight, cybersecurity agency Eclypsium stated in a report shared with The Hacker Information.
“These units are each highly effective, [and] usually extremely susceptible,” the researchers famous. “This has made MikroTik units a favourite amongst risk actors who’ve commandeered the units for every little thing from DDoS assaults, command-and-control (aka ‘C2’), site visitors tunneling, and extra.”
MikroTik units are an attractive goal not least as a result of there are greater than two million of them deployed worldwide, posing an enormous assault floor that may be leveraged by risk actors to mount an array of intrusions.
Certainly, earlier this September, reviews emerged of a brand new botnet named Mēris that staged a record-breaking distributed denial-of-service (DDoS) assault towards Russian web firm Yandex through the use of community units from Mikrotik as an assault vector by exploiting a now-addressed safety vulnerability within the working system (CVE-2018-14847).
The listing of 4 vulnerabilities found over the past three years and which might allow full takeover of MikroTik units is under –
- CVE-2019-3977 (CVSS rating: 7.5) – MikroTik RouterOS inadequate validation of improve package deal’s origin, permitting a reset of all usernames and passwords
- CVE-2019-3978 (CVSS rating: 7.5) – MikroTik RouterOS inadequate protections of a vital useful resource, resulting in cache poisoning
- CVE-2018-14847 (CVSS rating: 9.1) – MikroTik RouterOS listing traversal vulnerability within the WinBox interface
- CVE-2018-7445 (CVSS rating: 9.8) – MikroTik RouterOS SMB buffer overflow vulnerability
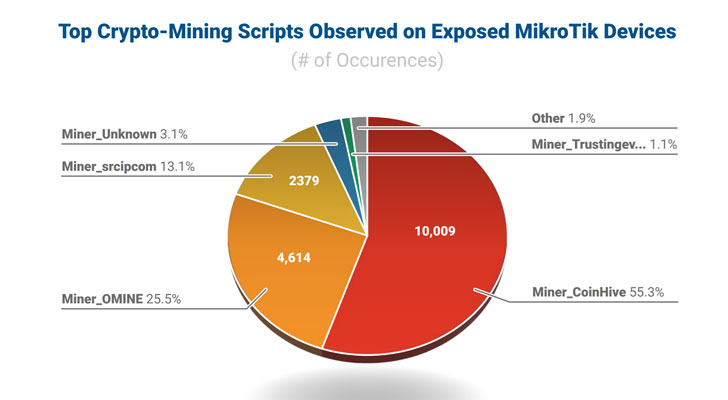
As well as, Eclypsium researchers stated they discovered 20,000 uncovered MikroTik units that injected cryptocurrency mining scripts into net pages that customers visited.
“The power for compromised routers to inject malicious content material, tunnel, copy, or reroute site visitors can be utilized in a wide range of extremely damaging methods,” the researchers stated. “DNS poisoning might redirect a distant employee’s connection to a malicious web site or introduce a machine-the-middle.”
“An attacker might use well-known strategies and instruments to doubtlessly seize delicate data reminiscent of stealing MFA credentials from a distant consumer utilizing SMS over WiFi. As with earlier assaults, enterprise site visitors might be tunneled to a different location or malicious content material injected into legitimate site visitors,” the researchers added.
MikroTik routers are removed from the one units to have been co-opted right into a botnet. Researchers from Fortinet this week disclosed how the Moobot botnet is leveraging a recognized distant code execution (RCE) vulnerability in Hikvision video surveillance merchandise (CVE-2021-36260) to develop its community, and use the compromised units to launch distributed denial-of-service (DDoS) assaults.