Hackers Hijack E-mail Reply Chains on Unpatched Alternate Servers to Unfold Malware
A brand new e mail phishing marketing campaign has been noticed leveraging the tactic of dialog hijacking to ship the IceID info-stealing malware onto contaminated machines by making use of unpatched and publicly-exposed Microsoft Alternate servers.
“The emails use a social engineering strategy of dialog hijacking (often known as thread hijacking),” Israeli firm Intezer stated in a report shared with The Hacker Information. “A solid reply to a earlier stolen e mail is getting used as a solution to persuade the recipient to open the attachment. That is notable as a result of it will increase the credibility of the phishing e mail and should trigger a excessive an infection fee.”
The most recent wave of assaults, detected in mid-March 2022, is alleged to have focused organizations inside vitality, healthcare, regulation, and pharmaceutical sectors.
IceID, aka BokBot, like its counterparts TrickBot and Emotet, is a banking trojan that has advanced to develop into an entry level for extra subtle threats, together with human-operated ransomware and the Cobalt Strike adversary simulation instrument.
It is able to connecting to a distant server and downloading next-stage implants and instruments that permit attackers to hold out follow-on actions and transfer laterally throughout affected networks to distribute further malware.
In June 2021, enterprise safety agency Proofpoint disclosed an evolving tactic within the cybercrime panorama whereby preliminary entry brokers have been noticed infiltrating goal networks by way of first-stage malware payloads reminiscent of IcedID to deploy Egregor, Maze, and REvil ransomware payloads.
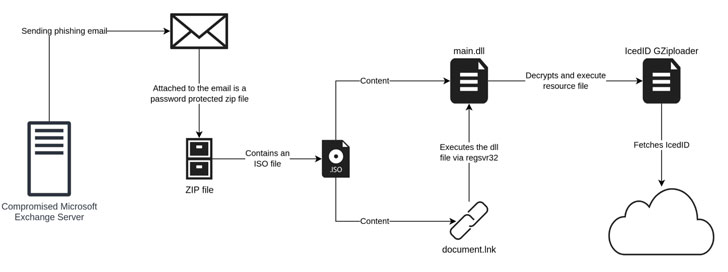
Whereas earlier IcedID campaigns have taken benefit of web site contact kinds to ship malware-laced hyperlinks to organizations, the present model of the assaults financial institution on weak Microsoft Alternate servers to ship the lure emails from a hijacked account, indicating an extra evolution of the social engineering scheme.
“The payload has additionally moved away from utilizing Workplace paperwork to the usage of ISO recordsdata with a Home windows LNK file and a DLL file,” researchers Joakim Kennedy and Ryan Robinson stated. “Using ISO recordsdata permits the risk actor to bypass the Mark-of-the-Internet controls, leading to execution of the malware with out warning to the person.”
The concept is to ship fraudulent replies to an already current e mail thread plundered from the sufferer’s account through the use of the compromised particular person’s e mail tackle to make the phishing emails seem extra professional.
“Using dialog hijacking is a strong social engineering method that may enhance the speed of a profitable phishing try,” the researchers concluded. “By utilizing this strategy, the e-mail seems extra professional and is transported via the conventional channels which may additionally embrace safety merchandise.”